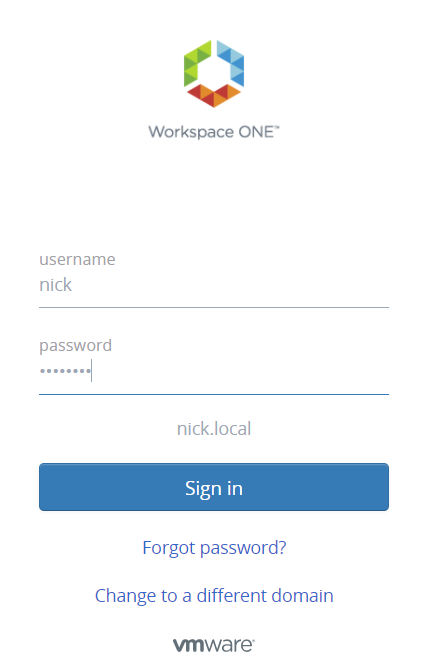
So you went through the process of getting Workspace ONE Access setup for MFA/RADIUS authentication. You sign into WSO-A, get MFA’d, and you jump for joy! But when you launch a virtual app, you are prompted for your password again…
The prompt is happening because RADIUS is not recognized as a valid method for password caching, which is used for the Windows-based login for the virtual app. Password caching, you guessed it, only works when password is defined as part of your access policy. But if we do Password+RADIUS, won’t it result in getting prompted for password twice during authentication? Yes… but there is a way around this.
Your first thought may be that you need to deploy True SSO, which would certainly work, but sometimes that can be a bit of a challenge if you do not already have a production-ready PKI architecture.
But do not fear – your RADIUS provider may have a way for you to enable Password+RADIUS without the need to get prompted twice! Duo just happens to be one of these providers, where you can customize the RADIUS configuration to ONLY prompt for the MFA push without Duo first requiring the password. Beautiful!
This will require a few things, which we will cover in more detail:
- Ensure password caching is allowed.
- Enable each WSO Connector to use auth chaining for its RADIUS authenticator. This allows the username captured from the initial prompt to be passed to Duo via RADIUS, so that Duo immediately sends an MFA without needing to authenticate the user against AD.
- Configure the Duo proxy to allow for this (if not using Duo, check with your RADIUS provider if this is possible).
- Configure the access policy for Password + RADIUS so that password caching works.
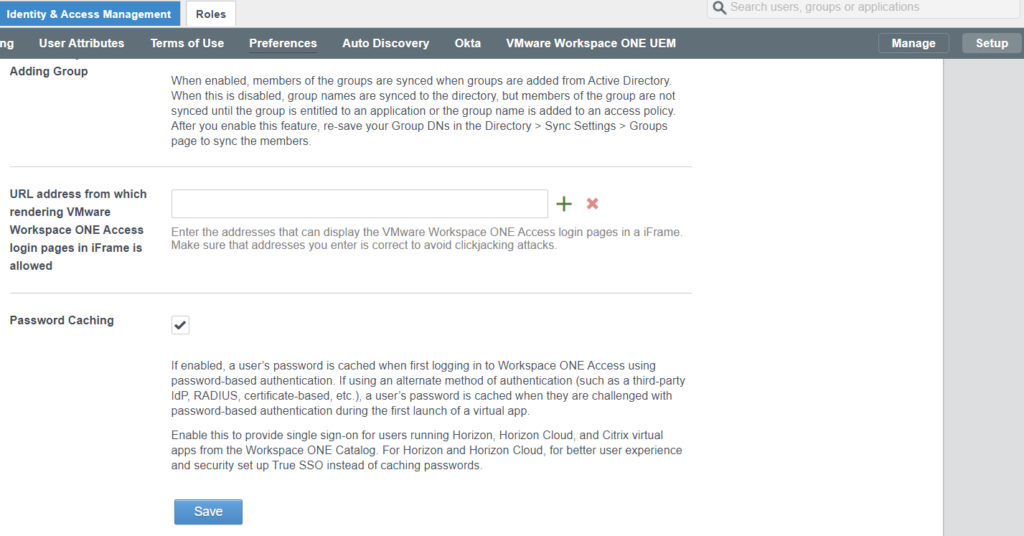
Ensure Password Caching is allowed
Head to WSO Access admin portal. Under I&AM, go to Setup > Preferences. Enable Password Caching if disabled. Note this is available in SaaS tenants after June 2020.
Enable RADIUS Authentication Chaining
Under I&AM > Setup, go to Legacy Connectors (as of this post, only Legacy Connectors/19.03.x are supported with Virtual Apps). Select the worker URL.
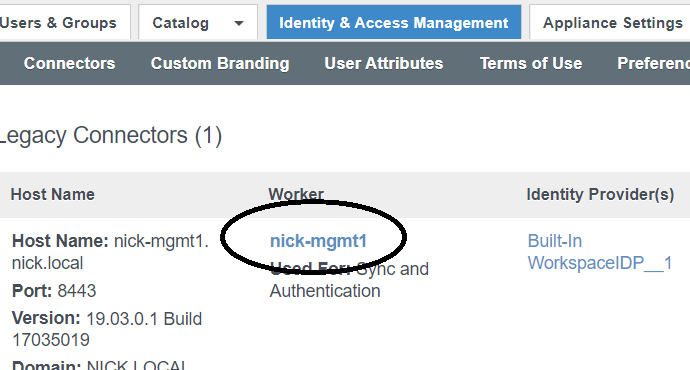
Under Auth Adapters, select the RadiusAuthAdapter. You will be directed to your Connector management page, so you will need access to your Connector.
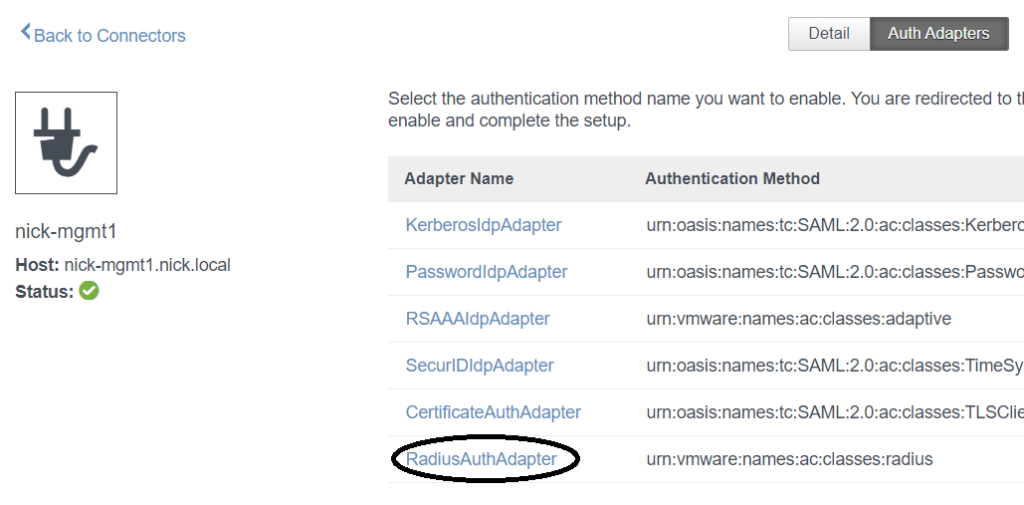
If auth chaining is not enabled, enable it:
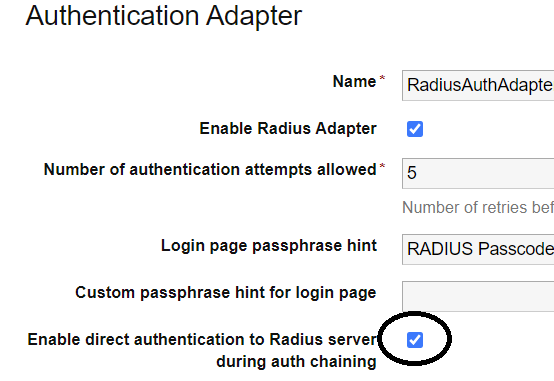
Repeat for each Connector.
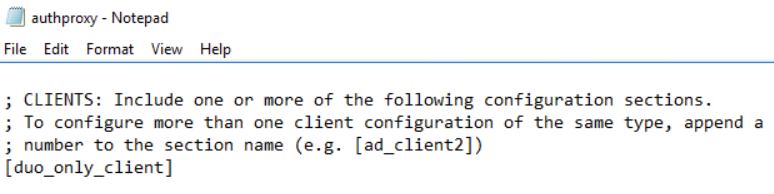
Configure Duo Proxy for Duo Only
In your authproxy config file, use duo_only_client. This prevents the need to query AD for the username/password for validation prior to the MFA prompt.
Additionally, you will need to set your RADIUS server to point to the duo_only_client by placing client=duo_only_client in the authproxy config, NOT Active Directory (notice I commented it out). Radius_ip_1 should be your WSO Connector, as it will be the one doing the RADIUS requests to your Duo auth proxy. If using a load balancer, this could be your SNIP, self-IP, etc. Duo also accepts IP ranges and CIDR notation here.
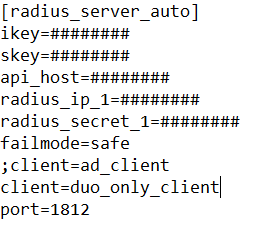
Note that if you have multiple RADIUS clients for various services, you can append a number to the name and match that to the Duo RADIUS server to use. This is useful if you’re using Duo for multiple applications outside of just WSO Access.
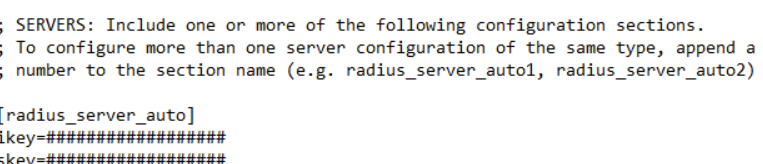
See here for Duo’s official configuration reference guide.
Save the config file. Restart the Duo proxy service.
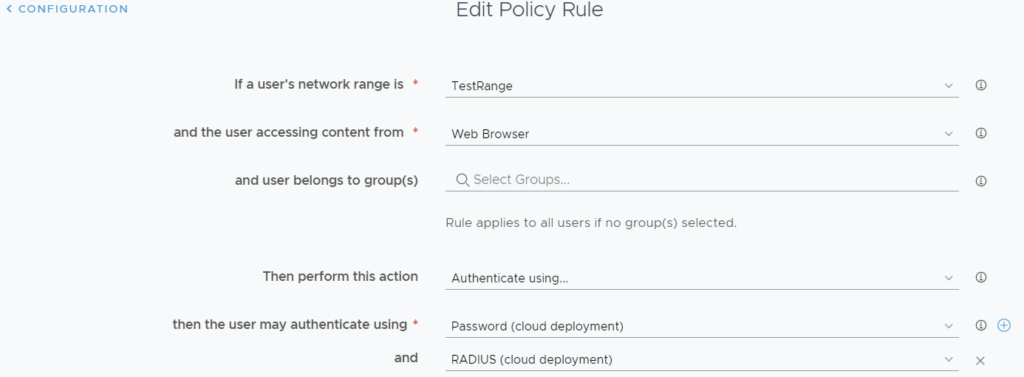
Configure your access policy for password + RADIUS
If everything was setup correctly, you should now be able to prompt for username+password on initial prompt, and then Duo for the next. Just setup the access policy to allow for this.
Head over to I&AM > Manage > Policies. If using more than the default policy, select the appropriate one(s) and select edit.
Select the appropriate network range(s) and change to Password (cloud deployment) + RADIUS (cloud deployment). Edit each policy/range as needed and save.
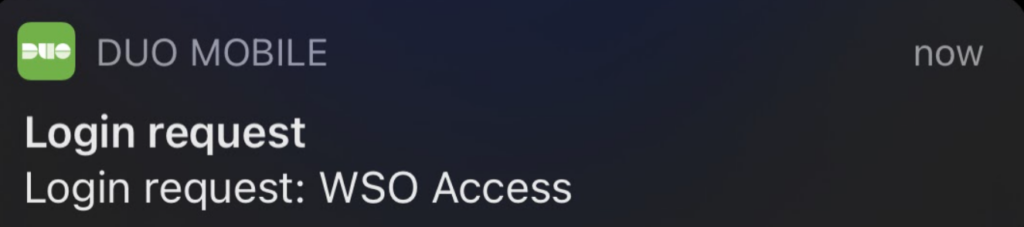
From a client that matches your network range/policy for MFA, let’s see what it looks like:
Hey, look! Duo prompt on my phone! Looking good…
Accepted and I am in the user portal! Now for the final test…
And just like that, I’m in! No additional password prompts for launch and no True SSO required!
Summary
This is a quick and easy way to allow for RADIUS MFA without the need of deploying True SSO. It is nice that Duo allows for the flexibility of MFA without the need of validating against AD first. If not using Duo, consult your RADIUS provider’s documentation to see if they allow for MFA without username/password validation first. Enjoy!