In my previous post, I talked about how we can utilize OPSWAT MetaDefender to act as a man-in-the-middle for our IdP, in this case Entra, to help secure BYOD devices. The downside with this method is that it’s pretty cumbersome to setup, so why not add OPSWAT as a second IdP instead?
Well, when I tried to setup OPSWAT’s IdP/MFA method, it would not accept WS1 Access’ SP metadata. A few days after opening a ticket with them, support was able to point me in the right direction! OPSWAT currently requires organization data to be added to the SP metadata. This includes Organization name, Organization Display Name, and Organization URL. These can be anything. Just add these after the SPSSODescriptor section near the end, like so, before uploading your WS1 Access SP metadata to OPSWAT:
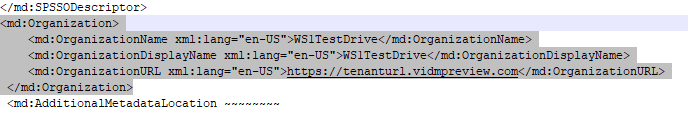
Now OPSWAT should accept your WS1 Access SP metadata under Secure Access > Access Methods > IdP MFA and let you continue!
Grab the IdP metadata from OPSWAT, and create a new SAML Identity Provider in Access. Copy the XML-based metadata and configure everything like below. In the bottom section, you’ll notice we’re sending the subject over to OPSWAT after the Entra auth succeeds, so we’re essentially up-auth’ing.
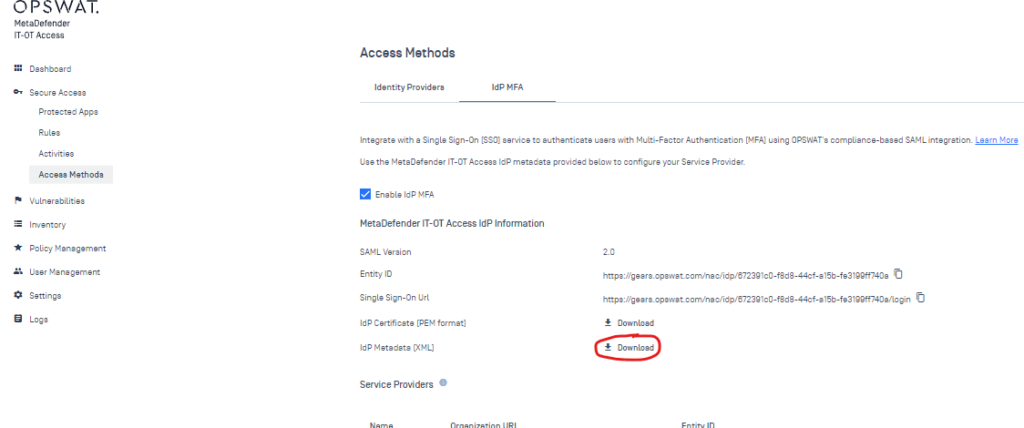
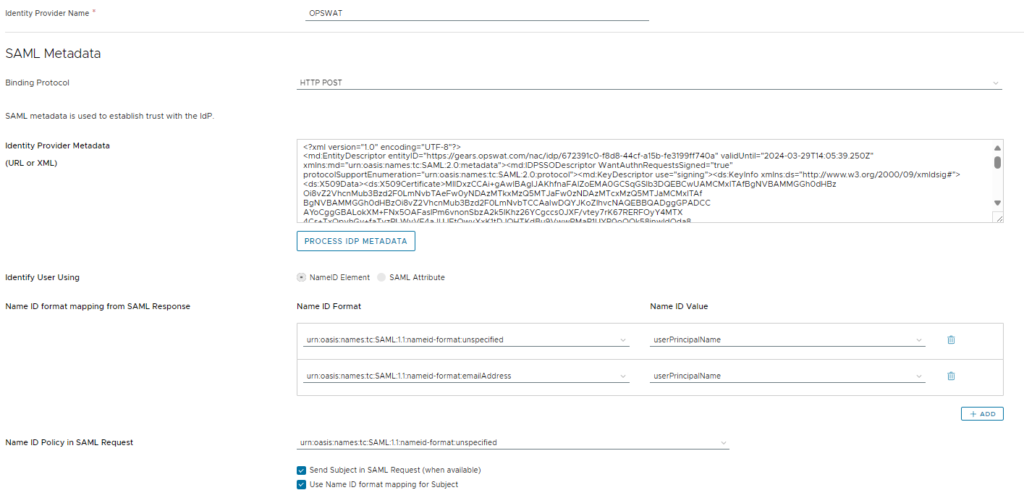
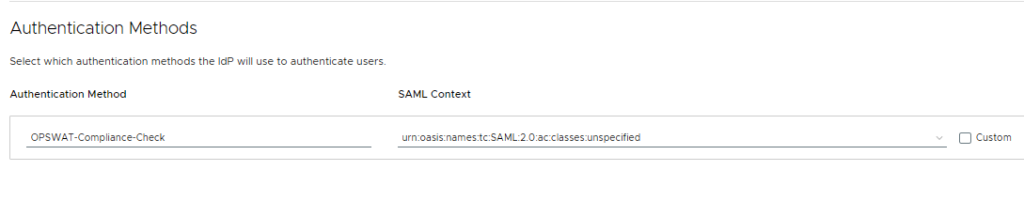
Then, head to your Access policy and add OPSWAT as a second authentication mechanism. You can add it to a specific network range on your default policy, or even apply it to individual apps via app-assigned policies!
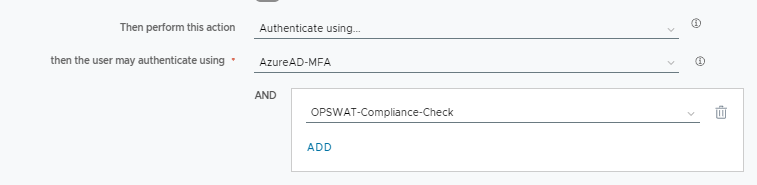
Just like before, if Entra auth succeeds, it then goes to OPSWAT for a compliance check. While we’re essentially doing the same thing as the previous post’s setup, this method is much cleaner and allows you to apply OPSWAT to individual apps within Access if needed! Hope this helps!